本文根据 https://zhuanlan.zhihu.com/p/683044464 创建一个WMI ACPI device编写,在实体机上测试通过。
- 原项目代码中有一点问题,需要修改 AcpiWmi.rc 中的代码最后一行为下面
MofResource MOFDATA AcpiWmi.def
2.编译后即可生成 AcpiWmi.dll

3.将这个文件放置到 c:\Windows\system32\drivers目录下
4.将如下 ASL 代码插入本机 ACPI DSDT 中()
Device(AAAA)
{
// pnp0c14 is pnp id assigned to WMI mapper
Name(_HID, "PNP0C14")
Name(_UID, "BBBB")
Name(_WDG, Buffer()
{
// MyMethod
// {8EC32B9D-EC6B-4138-91E8-8EB30C092E95}
0x9D, 0x2B, 0xC3, 0x8E, 0x6B, 0xEC, 0x38, 0x41, 0x91, 0xE8, 0x8E, 0xB3, 0x0C, 0x09, 0x2E, 0x95,
0x41, 0x41, // Object Id (AA)
1, // Instance Count
0x02, // Flags (WMIACPI_REGFLAG_METHOD)
// MyEvent
// {48149424-41F4-4D93-A725-F0E5C4724F8A}
0x24, 0x94, 0x14, 0x48, 0xF4, 0x41, 0x93, 0x4D, 0xA7, 0x25, 0xF0, 0xE5, 0xC4, 0x72, 0x4F, 0x8A,
0x80, // Object Id, NotificationValue
0x00, // Reserved
1, // Instance Count
0x08, // Flags (WMIACPI_REGFLAG_EVENT)
// Binary Mof
0x21, 0x12, 0x90, 0x05, 0x66, 0xd5, 0xd1, 0x11, 0xb2, 0xf0, 0x00, 0xa0, 0xc9, 0x06, 0x29, 0x10,
0x43, 0x43, // Object Id (CC)
0x01,
0x00
})
Name(WQCC, Buffer()
{
//Copy binaray hex txt here
0x46, 0x4f, 0x4d, 0x42, 0x01, 0x00, 0x00, 0x00, 0xbd, 0x03, 0x00, 0x00, 0x28, 0x0c, 0x00, 0x00,
0x44, 0x53, 0x00, 0x01, 0x1a, 0x7d, 0xda, 0x54, 0x18, 0xd7, 0x85, 0x00, 0x01, 0x06, 0x18, 0x42,
0x10, 0x07, 0x10, 0x22, 0x21, 0x04, 0x12, 0x01, 0xa1, 0xc8, 0x2c, 0x0c, 0x86, 0x10, 0x38, 0x2e,
0x24, 0x15, 0x07, 0x85, 0x12, 0x02, 0xa1, 0xfe, 0x04, 0xf2, 0x2b, 0x00, 0xa1, 0x43, 0x01, 0x32,
0x05, 0x18, 0x14, 0xe0, 0x14, 0x41, 0x04, 0xbd, 0x0a, 0xb0, 0x29, 0xc0, 0xa4, 0x00, 0x8b, 0x02,
0xb4, 0x0b, 0xb0, 0x2c, 0x40, 0xb7, 0x00, 0xe9, 0xb0, 0x44, 0x24, 0x38, 0x4a, 0x0c, 0x38, 0x4a,
0x27, 0xb6, 0x70, 0xc3, 0x06, 0x2f, 0x14, 0x45, 0x33, 0x88, 0x92, 0xa0, 0x72, 0x01, 0xbe, 0x11,
0x04, 0x5e, 0xae, 0x00, 0xc9, 0x13, 0x90, 0x66, 0x01, 0x86, 0x05, 0x58, 0x17, 0x20, 0x7b, 0x08,
0x54, 0xea, 0x10, 0x50, 0x72, 0x86, 0x80, 0x1a, 0x40, 0xab, 0x13, 0x10, 0x7e, 0xa5, 0x53, 0x42,
0x12, 0x84, 0x33, 0x56, 0xf1, 0xf8, 0x9a, 0x45, 0xd3, 0x73, 0x92, 0x73, 0x0c, 0x39, 0x1e, 0x17,
0x7a, 0x58, 0x08, 0x0d, 0x20, 0x2c, 0xd2, 0x90, 0x25, 0x77, 0xd1, 0x04, 0x86, 0x71, 0x79, 0x2c,
0xde, 0xbb, 0x80, 0x11, 0x23, 0x65, 0x03, 0x32, 0x44, 0x49, 0x70, 0xa8, 0x51, 0x5b, 0xa2, 0x00,
0xf3, 0xe3, 0xd0, 0xec, 0xda, 0x1e, 0x0b, 0x81, 0x64, 0xd2, 0x86, 0x82, 0x92, 0x02, 0xa1, 0xb1,
0x9d, 0xa9, 0x67, 0x14, 0xf1, 0x48, 0x0d, 0x93, 0xc0, 0xa3, 0x88, 0x6c, 0x34, 0x0e, 0x8d, 0x1d,
0x86, 0x87, 0x19, 0xec, 0x20, 0x0e, 0xe3, 0x98, 0x23, 0x27, 0xf0, 0x84, 0x8e, 0xf4, 0xc8, 0x0b,
0x9b, 0xa7, 0x50, 0x63, 0x34, 0x07, 0x45, 0x42, 0x1c, 0x05, 0xd0, 0x63, 0x0a, 0x7b, 0xb4, 0xb1,
0xcf, 0xd7, 0xc2, 0x07, 0x2b, 0x8c, 0x23, 0x38, 0xae, 0x04, 0xff, 0xff, 0x33, 0x3f, 0x83, 0x53,
0x88, 0x16, 0xa1, 0xa0, 0x7b, 0x80, 0x30, 0x62, 0x1e, 0x52, 0x94, 0x80, 0xf1, 0x62, 0x84, 0x88,
0x7a, 0x54, 0x06, 0x0c, 0x14, 0x24, 0xd0, 0x59, 0xc5, 0x88, 0x52, 0x34, 0x98, 0x20, 0x03, 0x7b,
0x02, 0xc6, 0x88, 0x17, 0xe2, 0x69, 0xe0, 0xa8, 0x8c, 0xd3, 0x33, 0x8c, 0x4e, 0x01, 0xd8, 0x79,
0x1c, 0x12, 0x46, 0x06, 0x84, 0x10, 0xcf, 0xe4, 0x58, 0x4d, 0x60, 0xf7, 0x37, 0x08, 0xe1, 0x9e,
0x50, 0x67, 0x02, 0x94, 0x09, 0x50, 0x38, 0x3c, 0x8d, 0xac, 0x2d, 0x20, 0xa2, 0x0d, 0x47, 0x28,
0xc7, 0xd8, 0x18, 0x9a, 0x10, 0xa3, 0x44, 0x8b, 0x12, 0x2c, 0x8a, 0x81, 0x0d, 0x17, 0xeb, 0x4c,
0x63, 0x9e, 0xaa, 0xc1, 0x03, 0xc5, 0x68, 0x4d, 0x80, 0xfd, 0x41, 0x90, 0x70, 0x27, 0x03, 0x49,
0x38, 0x1b, 0x78, 0x34, 0xa8, 0x63, 0x83, 0x4f, 0x07, 0x3e, 0x19, 0x3c, 0x2d, 0x78, 0x54, 0xe7,
0x16, 0xe4, 0x8c, 0x0f, 0xec, 0x61, 0xe2, 0xb1, 0xc0, 0x07, 0x00, 0x36, 0x35, 0xff, 0x14, 0x7c,
0x4e, 0xc0, 0xbb, 0x06, 0xd4, 0x05, 0xe1, 0xf1, 0x80, 0x0d, 0x33, 0x1c, 0x66, 0x88, 0x9e, 0x75,
0xb8, 0x13, 0x38, 0x44, 0x06, 0xe8, 0x39, 0x3d, 0x19, 0x60, 0x07, 0x76, 0x32, 0x8f, 0x05, 0x6f,
0x16, 0xcd, 0xde, 0x29, 0x08, 0xc1, 0xf1, 0xf8, 0x3a, 0xc1, 0x26, 0x9c, 0xc0, 0xf2, 0x07, 0x81,
0x1a, 0x99, 0xa1, 0x7d, 0xb7, 0x38, 0xad, 0xd7, 0x02, 0x1f, 0x00, 0x4c, 0x60, 0xb1, 0x10, 0x52,
0x00, 0xa1, 0xf1, 0x80, 0x5f, 0xf1, 0x11, 0x84, 0xdc, 0x1d, 0x3c, 0x5f, 0x9f, 0x48, 0xb0, 0xff,
0xff, 0xf3, 0x09, 0xbc, 0x31, 0xf9, 0xbe, 0x70, 0x4c, 0xcf, 0x14, 0x0c, 0xee, 0x20, 0x4e, 0x39,
0xc4, 0x03, 0x03, 0xe6, 0x8c, 0x02, 0x5c, 0x42, 0xad, 0x54, 0x9f, 0x19, 0x07, 0x02, 0x91, 0x8d,
0xb5, 0xfa, 0xdc, 0x41, 0xa5, 0x53, 0x49, 0xe3, 0x7c, 0x34, 0x58, 0xdf, 0x22, 0x70, 0x82, 0xc1,
0x74, 0xb8, 0xe1, 0x52, 0x29, 0x24, 0x14, 0x42, 0xe3, 0x31, 0xb8, 0xa5, 0xc1, 0x51, 0x10, 0x8f,
0xdf, 0xb1, 0x21, 0xe4, 0xe4, 0x28, 0x80, 0x3a, 0x00, 0x78, 0x78, 0xe7, 0x73, 0x9e, 0xef, 0x09,
0x09, 0x1c, 0x13, 0x42, 0xa7, 0x07, 0x9f, 0x17, 0xf0, 0x57, 0x03, 0x1f, 0x04, 0xf8, 0xe8, 0x9e,
0x41, 0xc0, 0x72, 0x66, 0x61, 0x0b, 0x3c, 0x38, 0x1b, 0x3f, 0x6a, 0x10, 0x14, 0x5f, 0x3d, 0x7c,
0xf2, 0x30, 0x6a, 0x8c, 0x67, 0x10, 0xdf, 0x40, 0xd8, 0x59, 0x85, 0x0f, 0xc7, 0x1f, 0x19, 0x3a,
0x12, 0x32, 0x80, 0xf3, 0x48, 0xc0, 0x8f, 0x09, 0xf0, 0x27, 0xe2, 0x49, 0xfb, 0x00, 0x62, 0x02,
0x0b, 0x3c, 0x26, 0x80, 0x02, 0xc8, 0xb7, 0x02, 0x1f, 0x7c, 0x9e, 0x0c, 0xd8, 0xff, 0x7f, 0x0e,
0xcf, 0x3e, 0x3e, 0xf9, 0xb0, 0x91, 0x22, 0xc6, 0x2f, 0x0b, 0x20, 0x92, 0x35, 0x2e, 0xd4, 0x70,
0x7d, 0x66, 0x60, 0x37, 0x06, 0xdc, 0xa0, 0x5e, 0x19, 0x7c, 0x18, 0x30, 0xac, 0x0f, 0x00, 0x1c,
0xd6, 0x68, 0x61, 0x4f, 0xf6, 0x69, 0xc2, 0x83, 0xf5, 0xcc, 0x7c, 0x8d, 0xf1, 0x19, 0x04, 0x2c,
0x80, 0x78, 0xef, 0x57, 0x01, 0x32, 0x01, 0x03, 0xb2, 0xa3, 0xce, 0x43, 0x01, 0x58, 0x3c, 0x4e,
0x87, 0x5c, 0x70, 0x70, 0x07, 0x0e, 0x63, 0x44, 0x79, 0x86, 0xe0, 0x30, 0xb1, 0xc3, 0xfa, 0xd8,
0xe2, 0x33, 0x80, 0x0f, 0x26, 0xec, 0x90, 0x83, 0x1d, 0x56, 0x7c, 0x43, 0x24, 0x18, 0xec, 0xe9,
0x60, 0x02, 0xc5, 0x59, 0xac, 0xa2, 0xc0, 0xa0, 0x8e, 0x4d, 0xc0, 0x3b, 0xc0, 0x49, 0x09, 0x94,
0x83, 0xc5, 0xff, 0xff, 0x47, 0xca, 0x26, 0x8d, 0x03, 0x3a, 0x7b, 0xec, 0xa1, 0xc9, 0x83, 0x86,
0x75, 0xac, 0x02, 0xe7, 0xa1, 0x09, 0x36, 0xe8, 0x8b, 0xd2, 0xb3, 0x52, 0x8c, 0xb0, 0x21, 0x9e,
0x32, 0x42, 0xbc, 0x31, 0xb1, 0x13, 0x4b, 0x14, 0x36, 0xd0, 0x60, 0xcf, 0x1a, 0x51, 0x5e, 0x2f,
0x7a, 0xc3, 0xd3, 0x6d, 0x29, 0x4a, 0xb4, 0xc3, 0x78, 0xc0, 0x88, 0x72, 0xa2, 0xf1, 0x42, 0x19,
0x23, 0xd2, 0x09, 0x04, 0x7c, 0x68, 0x62, 0xe1, 0x1f, 0x2c, 0x3a, 0x17, 0xf8, 0xd0, 0x04, 0x70,
0xe3, 0xff, 0x7f, 0xd3, 0x21, 0x27, 0x0c, 0x9d, 0x7c, 0xf0, 0x97, 0x05, 0x0c, 0xc1, 0xc0, 0x10,
0x3a, 0xb4, 0x58, 0xd4, 0xa1, 0x05, 0x75, 0xb2, 0xf0, 0xa1, 0x82, 0xdd, 0x0a, 0x1e, 0x1a, 0xd8,
0x99, 0x05, 0x73, 0x50, 0x01, 0xff, 0x11, 0x07, 0x77, 0xcc, 0x80, 0x7b, 0xab, 0xc0, 0xcd, 0x88,
0x1f, 0x7f, 0xc0, 0x79, 0x19, 0xf2, 0xa1, 0x0b, 0x9c, 0xa7, 0x2a, 0xdc, 0x99, 0x0b, 0x78, 0x8c,
0x09, 0x77, 0xcc, 0x04, 0xc7, 0xa0, 0xd8, 0x11, 0x13, 0x96, 0x42, 0x9b, 0x3e, 0x35, 0x1a, 0xb5,
0x6a, 0x50, 0xa6, 0x46, 0x99, 0x06, 0xb5, 0xfa, 0x54, 0x6a, 0xcc, 0x98, 0x87, 0xa1, 0xf9, 0x81,
0xa0, 0x13, 0x82, 0x23, 0x82, 0xd0, 0xff, 0x7f, 0x80, 0x67, 0x82, 0x8c, 0x1c, 0x71, 0x0c, 0x22,
0x20, 0x8b, 0x35, 0x01, 0xc2, 0xa2, 0x82, 0x70, 0x15, 0x20, 0xec, 0xff, 0x0f
})
// Storage for 1 instances of ULONG
Name(AADD, 0)
//
// MyMethod data block
// Arg0 has the instance being queried
// Arg1 has the method id
// Arg2 has the data passed
Method(WMAA, 3)
{
Store(Arg2, AADD)
Notify(AAAA, 0x80)
Return(0)
}
// More info about an event
// Arg0 is the event id that was fired
Method(_WED, 1)
{
Return(AADD)
}
}
5.编译加载修改后的 DSDT, 然后使用 ASL.exe Load 到本机。需要注意,在 Windows 11中需要打开测试模式(bcdedit /set testsigning on)
6.重启之后,确认可以在设备管理器中出现了我们的设备
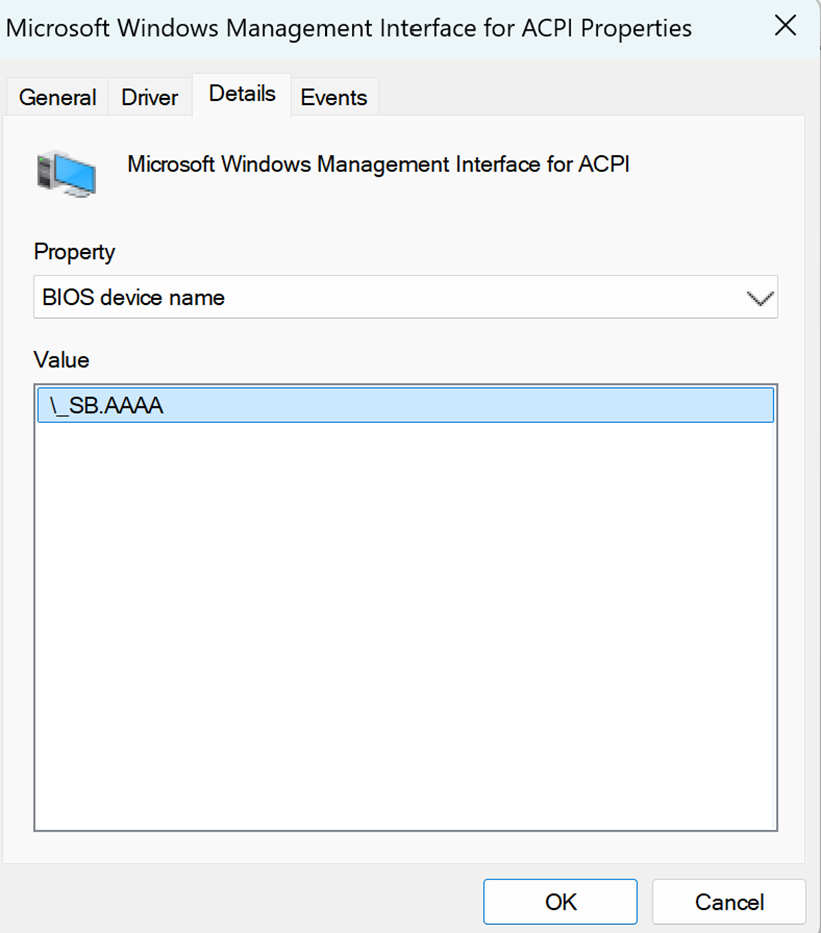
7.之后,以管理员权限运行 WMICreator, 在 Receive an event 页面,选择 root\WMI(有时候需要等待一下才能出现),然后 Event Class 上选择 “AcpiWmi_MyEvent”, 然后点击Execute Code 就在等待事件了

8.接下来再以管理员权限运行一个 WMICreator, 在 Execute a method 页面,Namespace 选择“root\WMI”, Classes withmethods 选择 “AcpiWmi_MyMethod”, Method 中选择FireEvent, 接下来 Method [in] parameters 随便输入一个数字, 点击Execute Code 即调用了 ACPI 中的Method

特别注意:这里必须再上面设置 hack= XXX, 然后下面的 instance 也选中,否则在运行的时候会出现错误提示!
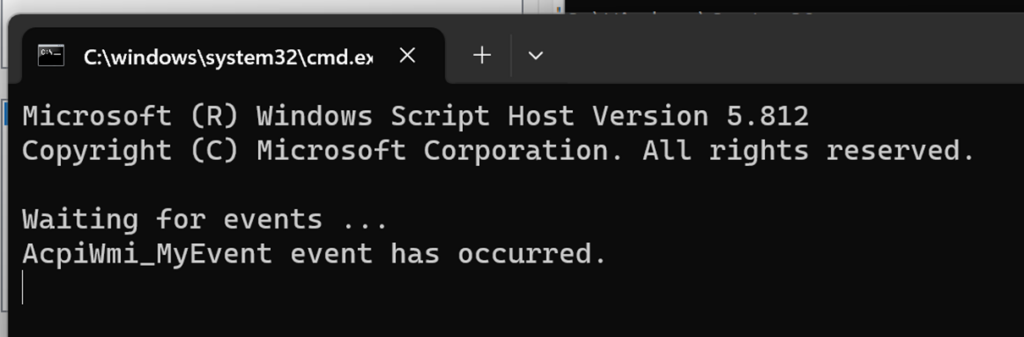
9.最后我们在第一个打开的 WMI Creator 中看到有事件发生:
本文提到的,修改后的完整代码: