本文介绍如何使用USB 键盘在 Windows 下生成一个 Dump 文件,然后通过工具进行分析。
在【参考1】,微软提供了一个使用键盘触发蓝屏生成 Dump 文件的方法。具体操作是:
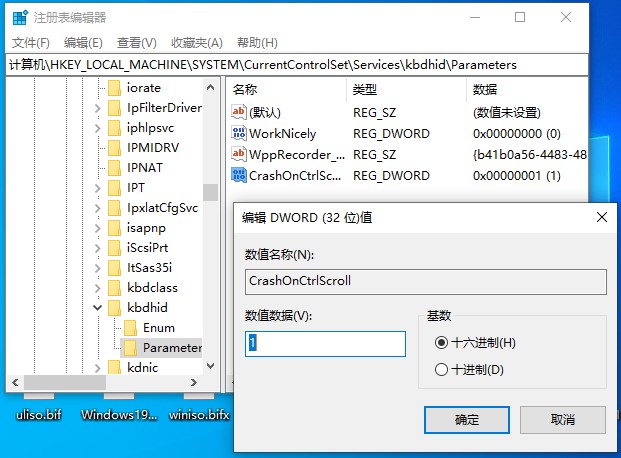
1.对于 USB 键盘,需要在注册表:HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\kbdhid\Parameters 下面创建 CrashOnCtrlScroll 类型为 REG_DWORD ,值为0x01:
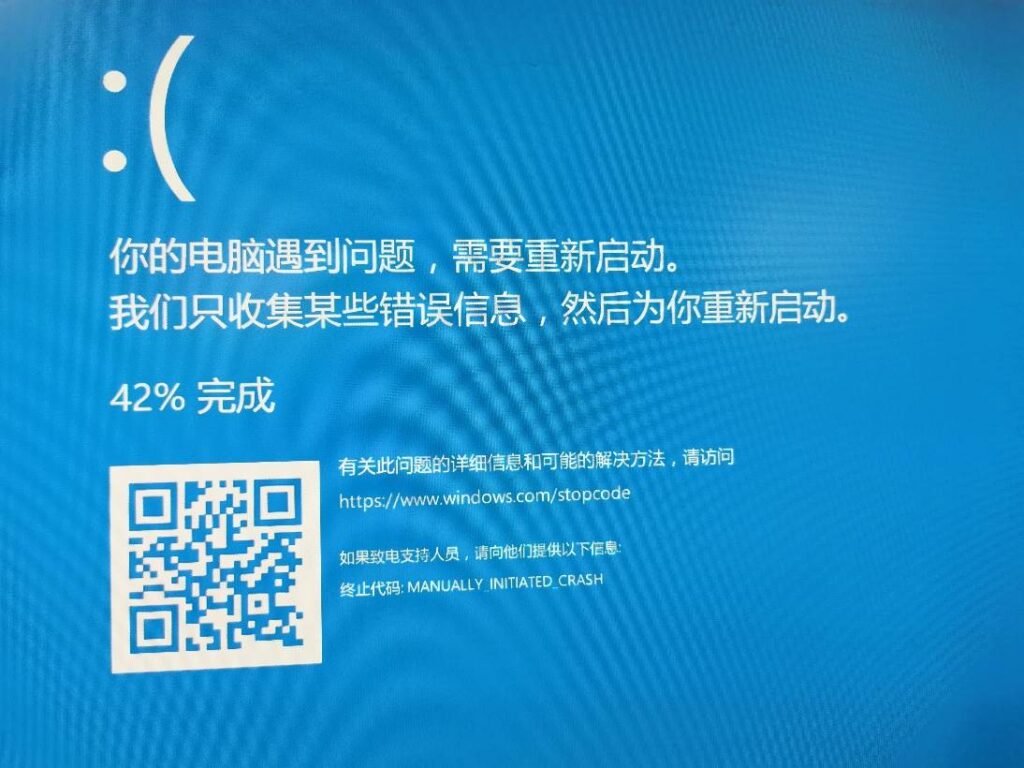
2.重启之后可以通过按下右侧 ctrl 然后快速按下2次 Scroll 键实现蓝屏:
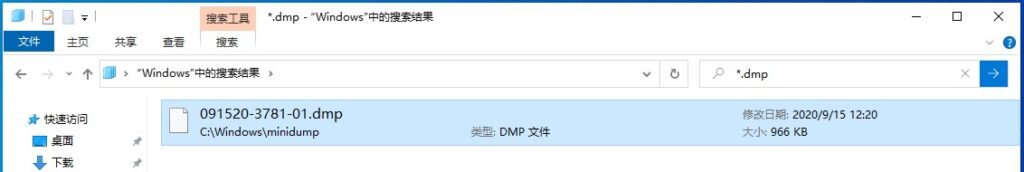
3.重启后在被测机的 Windows 目录下查找 *.dmp 文件:
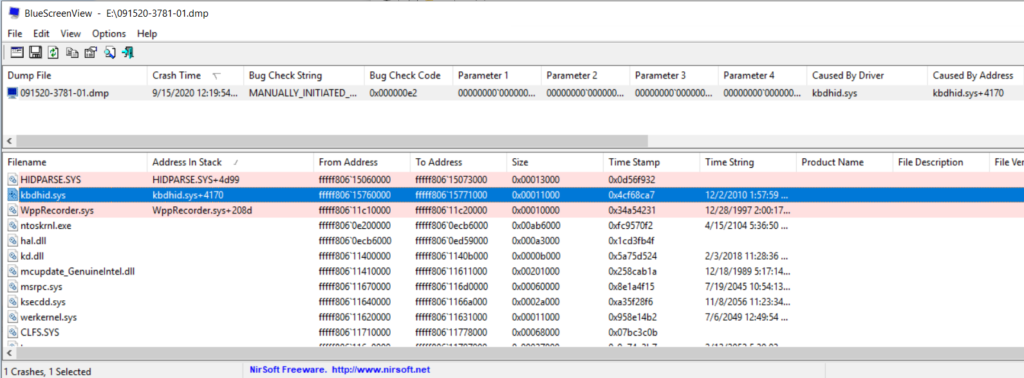
4.可以使用nirsoft的 BlueScreenView v1.55 【参考2】,进行简单的分析,使用方法很简单:打开文件然后将 Dump 文件放进去。从下面可以看到,蓝屏是 kbdhid.sys 文件导致的:
5.正规的方法是使用 WinDBG,在下面的位置打开 dump 文件
运行结果:
Executable search path is:
Windows 10 Kernel Version 18362 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff806`0e200000 PsLoadedModuleList = 0xfffff806`0e648210
Debug session time: Tue Sep 15 12:19:54.203 2020 (UTC + 8:00)
System Uptime: 0 days 0:00:13.012
Loading Kernel Symbols
...............................................................
................................................................
................................
Loading User Symbols
Loading unloaded module list
......
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff806`0e3c1220 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:fffff806`1309acc0=00000000000000e2
之后运行 !analyze -v 命令
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
MANUALLY_INITIATED_CRASH (e2)
The user manually initiated this crash dump.
Arguments:
Arg1: 0000000000000000
Arg2: 0000000000000000
Arg3: 0000000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
STACK_TEXT:
fffff806`1309acb8 fffff806`15764170 : 00000000`000000e2 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KeBugCheckEx
fffff806`1309acc0 fffff806`15763a7f : ffffa80e`a2d0d602 fffff806`11c1208d ffffa80e`a2d321d0 00000000`000000c0 : kbdhid!KbdHidProcessCrashDump+0x1f0
fffff806`1309ad00 fffff806`15064d99 : ffffa80e`a2d0d6a0 ffffa80e`a2e6ac4c ffffa80e`00000000 fffff806`15068110 : kbdhid!KbdHid_InsertCodesIntoQueue+0xbf
fffff806`1309ad60 fffff806`15064f09 : ffffa80e`000000c6 fffff806`0e231f39 ffffa80e`a2c51470 00000000`00000001 : HIDPARSE!HidP_KbdPutKey+0x45
fffff806`1309ad90 fffff806`15065084 : ffffa80e`a2e6ac4c 00000000`0000000e ffffa80e`a2d30010 fffff806`15001a27 : HIDPARSE!HidP_ModifierCode+0xa9
fffff806`1309adc0 fffff806`15065173 : ffffa80e`a2e6ad18 ffffa80e`a2d2c6d0 ffffa80e`a2d2c6d0 fffff806`15063e9a : HIDPARSE!HidP_TranslateUsage+0x8c
fffff806`1309ae10 fffff806`157637b5 : 00000000`00000000 ffffa80e`a2d2c6d0 ffffa80e`a2d0d6a0 ffffa80e`a28fe300 : HIDPARSE!HidP_TranslateUsageAndPagesToI8042ScanCodes+0xb3
fffff806`1309ae80 fffff806`0e32b136 : 00000000`00000000 ffffa80e`a77aff02 ffffa80e`00000000 00000000`0007fe01 : kbdhid!KbdHid_ReadComplete+0x445
fffff806`1309af10 fffff806`0e247799 : ffffa80e`a2d2c6d0 fffff806`1309afe9 00000000`00000000 ffffa80e`a2d2cc6b : nt!IopUnloadSafeCompletion+0x56
fffff806`1309af40 fffff806`0e247667 : ffffa80e`a28fe310 00000000`00000006 00000000`00000000 ffffa80e`a2da21d0 : nt!IopfCompleteRequest+0x119
fffff806`1309b050 fffff806`1502acb1 : ffffa80e`a28fe300 ffffa80e`a28fe302 fffff806`1309b0f1 00000000`00000009 : nt!IofCompleteRequest+0x17
fffff806`1309b080 fffff806`1502a7ba : ffffa80e`a2da21d0 ffffa80e`a2da2102 ffffa80e`a290d730 00000000`00000009 : HIDCLASS!HidpDistributeInterruptReport+0x25d
fffff806`1309b150 fffff806`0e247799 : ffffa80e`a2d2f9a0 ffffa80e`a2d2f9a0 fffff806`1309b201 ffffa80e`a2d2fe1b : HIDCLASS!HidpInterruptReadComplete+0x34a
fffff806`1309b1f0 fffff806`0e247667 : ffffa80e`a2bc99b0 fffff806`14c48f00 00000000`00000001 00000000`00000001 : nt!IopfCompleteRequest+0x119
fffff806`1309b300 fffff806`11b383fd : 00000000`00000000 ffffa80e`a2bc89c0 00000000`00000002 fffff806`14c39700 : nt!IofCompleteRequest+0x17
fffff806`1309b330 fffff806`11b37ecb : ffffa80e`a2bc8b02 fffff806`1309b451 ffffa80e`a2d2f9a0 00000000`00000000 : Wdf01000!FxRequest::CompleteInternal+0x22d [minkernel\wdf\framework\shared\core\fxrequest.cpp @ 869]
fffff806`1309b3c0 fffff806`14c47e80 : 00000000`ffffff02 ffffa80e`a2bc89c0 ffffa80e`a2c28400 ffffa80e`a2c28400 : Wdf01000!imp_WdfRequestComplete+0x8b [minkernel\wdf\framework\shared\core\fxrequestapi.cpp @ 436]
fffff806`1309b420 fffff806`14c45cf4 : ffffa80e`a2bc8b60 ffffa80e`a2c28460 ffffa80e`a2bc8bf0 fffff806`1309b6f8 : USBXHCI!Bulk_Transfer_CompleteCancelable+0x19c
fffff806`1309b480 fffff806`14c44460 : ffffa80e`a25c97e0 00000000`00000003 00000000`00000000 fffff806`11c1208d : USBXHCI!Bulk_ProcessTransferEventWithED1+0x464
fffff806`1309b540 fffff806`14c398d3 : ffffa80e`a107e901 fffff806`14df8301 00000000`02400280 fffff806`1309b670 : USBXHCI!Bulk_EP_TransferEventHandler+0x10
fffff806`1309b570 fffff806`14c2ba4f : 00000000`0000002b fffff806`1309b661 ffffa80e`a2af58a0 fffff806`14c134b9 : USBXHCI!TR_TransferEventHandler+0x17
fffff806`1309b5a0 fffff806`14c4c2be : fffff806`1309b6f8 fffff806`1309b6c8 00000000`00000000 fffff806`1309b6d0 : USBXHCI!Endpoint_TransferEventHandler+0x167
fffff806`1309b620 fffff806`14c2ea3c : ffffa80e`a2969ab0 fffff806`1309b719 00000000`00000000 ffffa80e`a2b35510 : USBXHCI!UsbDevice_TransferEventHandler+0xa6
fffff806`1309b680 fffff806`14c2f55c : 00000000`00000000 00000000`00000001 00000000`00000000 ffffa80e`a29698b0 : USBXHCI!Interrupter_DeferredWorkProcessor+0x578
fffff806`1309b780 fffff806`11b326ad : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : USBXHCI!Interrupter_WdfEvtInterruptDpc+0xc
fffff806`1309b7b0 fffff806`0e26ae85 : fffff806`0bb04180 00000000`00000001 fffff806`1309b7a8 00000000`00000000 : Wdf01000!FxInterrupt::_InterruptDpcThunk+0x9d [minkernel\wdf\framework\shared\irphandlers\pnp\km\interruptobjectkm.cpp @ 410]
fffff806`1309b7f0 fffff806`0e26a4df : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiExecuteAllDpcs+0x305
fffff806`1309b930 fffff806`0e3c4d64 : 00000000`00000000 fffff806`0bb04180 fffff806`0e791400 ffffa80e`a6adf040 : nt!KiRetireDpcList+0x1ef
fffff806`1309bb60 00000000`00000000 : fffff806`1309c000 fffff806`13095000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x84
SYMBOL_NAME: kbdhid!KbdHidProcessCrashDump+1f0
MODULE_NAME: kbdhid
IMAGE_NAME: kbdhid.sys
IMAGE_VERSION: 10.0.18362.418
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 1f0
FAILURE_BUCKET_ID: MANUALLY_INITIATED_CRASH_kbdhid!KbdHidProcessCrashDump
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {a90fbd35-7a19-bced-0f76-fa89d249d332}
Followup: MachineOwner
---------
同样的,蓝屏原因指向 KBDHID.sys
参考:
- https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/forcing-a-system-crash-from-the-keyboard
- https://www.nirsoft.net/utils/blue_screen_view.html